Best hard disk encryption software is crucial in today’s digital age to protect sensitive information from unauthorized access. As we delve into the realm of encryption software, discover the key aspects that make these tools indispensable for safeguarding your data effectively.
Hard disk encryption software plays a vital role in ensuring the confidentiality and integrity of your data stored on hard drives. Understanding the features and types of encryption software available is essential to make an informed decision for securing your valuable information.
Introduction to Hard Disk Encryption Software
Hard disk encryption software is a type of security program designed to encrypt data stored on a computer’s hard drive. This encryption process converts the data into a form that can only be read with the correct decryption key, providing an additional layer of protection against unauthorized access.
Securing data on hard drives is crucial to prevent sensitive information from falling into the wrong hands. In case of theft or loss of a device, encrypted data remains inaccessible to anyone without the decryption key, safeguarding personal and confidential information.
Key Features of Hard Disk Encryption Software
- Full Disk Encryption: Encrypts the entire hard drive, including the operating system, to protect all data stored on the device.
- Strong Encryption Algorithms: Utilizes advanced encryption algorithms like AES (Advanced Encryption Standard) to ensure robust protection against unauthorized access.
- Pre-Boot Authentication: Requires users to authenticate themselves before the operating system loads, adding an extra layer of security.
- Centralized Management: Allows for centralized control and management of encryption policies across multiple devices, ideal for organizations with multiple endpoints.
- Secure Data Recovery: Provides options for secure data recovery in case of forgotten passwords or other issues, ensuring data accessibility without compromising security.
Types of Hard Disk Encryption Software
When it comes to hard disk encryption software, there are different types available to secure your data. Let’s explore the differences between full disk encryption and file-based encryption, as well as software-based and hardware-based encryption.
Full Disk Encryption vs. File-Based Encryption
Full disk encryption involves encrypting the entire hard drive, ensuring that all data on the disk is protected. On the other hand, file-based encryption allows you to selectively encrypt specific files or folders, providing more flexibility in terms of what you choose to secure.
- Full Disk Encryption:
- Encrypts the entire hard drive.
- Provides comprehensive protection for all data stored on the disk.
- Requires decryption of the entire drive to access any data.
- File-Based Encryption:
- Allows selective encryption of specific files or folders.
- Offers flexibility in choosing which data to encrypt.
- Enables access to unencrypted data without decrypting the entire drive.
Software-Based Encryption vs. Hardware-Based Encryption, Best hard disk encryption software
Software-based encryption utilizes encryption algorithms and software to secure data, while hardware-based encryption involves dedicated hardware components to handle encryption processes.
- Software-Based Encryption:
- Relies on encryption software to protect data.
- Offers flexibility and ease of implementation.
- May impact system performance due to software overhead.
- Hardware-Based Encryption:
- Uses dedicated hardware components for encryption.
- Provides faster encryption/decryption processes.
- Can be more secure against certain types of attacks.
Features to Consider
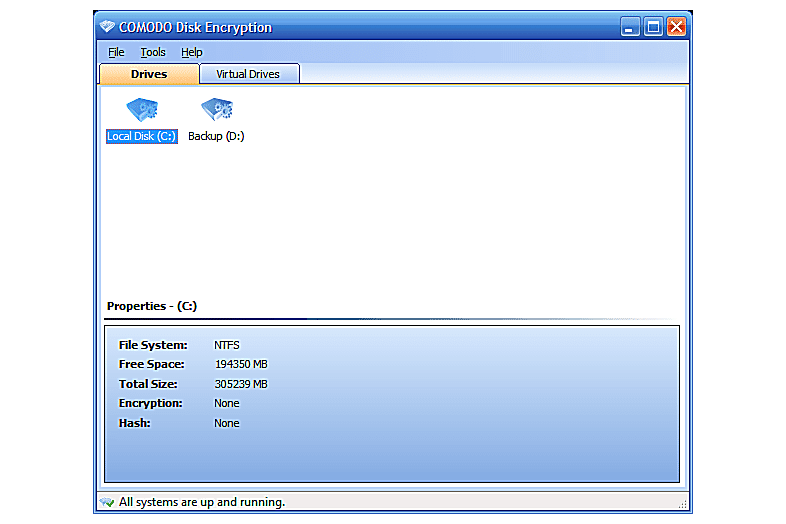
When choosing encryption software for your hard disk, it is essential to consider various features that can enhance the security and usability of the software. Here are some key features to keep in mind:
1. Encryption Strength
- Look for software that offers strong encryption algorithms such as AES-256, which is widely recognized as secure.
- Ensure that the software uses industry-standard encryption methods to protect your data effectively.
2. Multi-platform Support
- Choose software that is compatible with different operating systems, including Windows, macOS, and Linux, to ensure seamless encryption across all your devices.
- Consider cloud storage compatibility if you need to encrypt data stored in the cloud.
3. User-Friendly Interface
- Opt for software that offers an intuitive and easy-to-use interface, making it simple for you to encrypt and decrypt your data without complications.
- Look for features like drag-and-drop functionality and automatic encryption to streamline the encryption process.
4. Key Management
- Check if the software provides secure key management options, such as password protection, two-factor authentication, and key recovery mechanisms.
- Ensure that you have control over who can access the encrypted data and manage encryption keys securely.
5. Performance and Speed
- Consider the impact of encryption on your system’s performance and choose software that offers a balance between security and speed.
- Look for software that minimizes encryption and decryption times to maintain productivity levels.
Reputable Encryption Software Providers
Some examples of reputable encryption software providers include:
VeraCrypt, BitLocker, FileVault, Symantec Endpoint Encryption, and Sophos SafeGuard.
Compatibility with Operating Systems
Encryption software varies in compatibility with different operating systems. While some software may be designed specifically for Windows, others may cater to macOS or Linux users. It is crucial to choose software that aligns with your operating system requirements to ensure seamless encryption and decryption processes across your devices.
Installation and Setup
When it comes to installing and setting up hard disk encryption software, it is essential to follow the proper steps to ensure the security of your data. Below is a detailed guide on configuring encryption settings and best practices for ensuring that the encryption is properly set up.
General Steps for Installation and Setup
- Download the hard disk encryption software from a trusted source.
- Run the installer and follow the on-screen instructions to complete the installation process.
- Once installed, launch the software and begin the setup process.
- Choose a strong password for encryption to enhance security.
- Follow the prompts to select the drive or partition you want to encrypt.
- Configure any additional settings or options according to your preferences.
- Complete the setup process and restart your computer to apply the encryption.
Configuring Encryption Settings
- Choose the encryption algorithm that best suits your needs, such as AES or Twofish.
- Set the encryption strength, typically 128-bit or 256-bit, for enhanced security.
- Configure any additional security features, such as two-factor authentication or biometric verification.
- Define access controls and permissions for authorized users to access encrypted data.
- Regularly update the encryption software to ensure the latest security patches and features are applied.
Best Practices for Ensuring Proper Encryption Setup
- Regularly backup your data to prevent data loss in case of any issues with encryption.
- Use complex and unique passwords to prevent unauthorized access to encrypted data.
- Avoid sharing encryption keys or passwords with unauthorized individuals.
- Encrypt all sensitive data to maintain confidentiality and privacy.
- Periodically review and update encryption settings to adapt to changing security needs.
Performance and Impact on System
When it comes to using hard disk encryption software, there may be some impact on system performance due to the encryption processes running in the background. It is essential to understand how encryption software can affect your system and how to optimize performance while keeping your data secure.
Impact on System Performance
Encryption software can potentially slow down system performance, especially during tasks that involve reading or writing a large amount of data. This is because every piece of data being processed needs to be encrypted or decrypted, adding an extra layer of computation that can cause delays.
- Encryption overhead: The encryption and decryption processes can consume additional system resources, leading to slower read and write speeds.
- CPU usage: Encryption software can utilize a significant portion of the CPU, affecting the overall performance of the system.
- Boot time: Encrypting the entire hard disk can increase the time it takes for the system to boot up.
Optimizing System Performance
To optimize system performance while using encryption software, consider the following tips:
- Choose the right encryption algorithm: Some algorithms are more resource-intensive than others. Select an algorithm that balances security and performance.
- Hardware acceleration: Utilize hardware features like Trusted Platform Modules (TPM) or encryption accelerators if available to offload encryption tasks from the CPU.
- Regular maintenance: Keep your system clean and organized, removing unnecessary files and programs that could impact performance.
Maintaining System Efficiency with Encryption Enabled
To ensure your system remains efficient with encryption enabled, follow these best practices:
- Update software regularly: Keep your encryption software and operating system up to date to benefit from performance improvements and security patches.
- Monitor system performance: Use system monitoring tools to track resource utilization and identify any bottlenecks caused by encryption processes.
- Backup important data: In case of any performance issues or hardware failures, having a backup of your important data is crucial to prevent data loss.
Security and Reliability
When it comes to hard disk encryption software, security and reliability are paramount. Let’s delve into the security measures, data integrity, confidentiality, and reliability aspects of different encryption software options.
Security Measures
- Encryption Algorithms: Most encryption software uses advanced encryption algorithms such as AES (Advanced Encryption Standard) to secure data.
- Key Management: Secure key management is crucial for ensuring that only authorized users can access encrypted data.
- Two-Factor Authentication: Some encryption software offers two-factor authentication for an added layer of security.
- Secure Boot: Secure boot ensures that the system boots up securely and protects against unauthorized access.
Data Integrity and Confidentiality
- Hash Functions: Encryption software uses hash functions to verify data integrity and detect any unauthorized changes.
- Data Masking: Confidential data is masked to prevent unauthorized access and ensure confidentiality.
- Data Shredding: Some encryption software offers data shredding capabilities to securely delete sensitive information.
Reliability Factors
- Performance Impact: Evaluate the performance impact of encryption software on system speed and efficiency.
- Compatibility: Check the compatibility of encryption software with different operating systems and hardware configurations.
- Updates and Support: Reliable encryption software providers offer regular updates and customer support for any issues or concerns.
Final Summary

In conclusion, choosing the best hard disk encryption software is a proactive step towards enhancing your data security measures. By implementing robust encryption solutions, you can mitigate the risks of data breaches and unauthorized access, ultimately safeguarding your sensitive information effectively.
Question Bank: Best Hard Disk Encryption Software
What is the difference between full disk encryption and file-based encryption?
Full disk encryption secures the entire hard drive, while file-based encryption only encrypts specific files or folders.
Which encryption software providers are known for their reliability?
Some reputable encryption software providers include VeraCrypt, BitLocker, and Symantec.
How does encryption software impact system performance?
Encryption software can lead to a slight decrease in system performance, but optimizations can help mitigate any noticeable impact.
